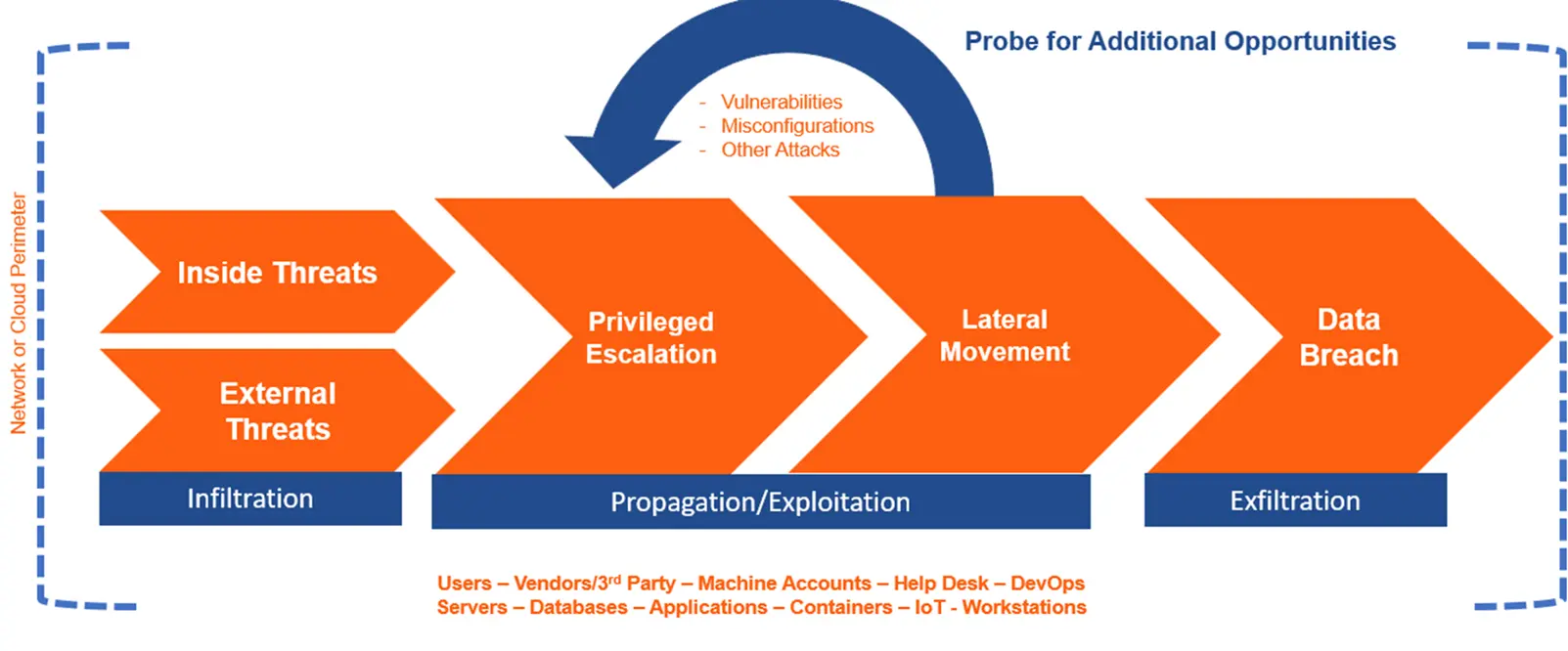

✓US-based Expert Ethical Hacking Team.
✓Videos to demonstrate successful exploits of your environment!
✓Executive Summary Reporting designed for C-Suite and 3rd party.
✓Use Mitigator to perform scans and create your own Vulnerability Management program!
✓US-based Expert Ethical Hacking Team.
✓Videos to demonstrate successful exploits of your environment!
✓Executive Summary Reporting designed for C-Suite and 3rd party.
✓Access to Mitigator Vulnerability Threat Manager Platform where you can:
➢Spot threat trends, analyze vulnerabilities, prioritize remediation from a central dashboard.
➢Create Remediation tickets in ServiceNOW™, Jira®, and Connectwise™.
➢Request "on-demand" Pen Testing of specific vulnerabilities (add-on feature).
➢Analyze vulnerabilities by asset and criticality.
➢Search & Drill-down by specific time periods, vulnerability, and other parameters.
➢Adjust risk scores based upon context and compensating controls for accurate risk ratings.
➢Request Remediation Assistance (add-on feature).
➢Export vulnerability data by date, source, criticality, etc.
✓Use Mitigator to perform scans and create your own Vulnerability Management Program!
24x7x365 US-based SOC/NOC
25+ years Regulatory Compliance experience (GLBA, PCI, HIPAA, NERC, AWIA, etc.)
SOC 2 Certified
Offering comprehensive cybersecurity Awareness Training Solutions
Managed Services for On-premise Data center, Cloud and Hybrid environments
Flexible pricing models that can be 24x7, 8x5, OR off-peak 7pm to 7am only coverage
MSP & MSSP Solutions for both IT & OT ICS environments
Certified Experts (CISSP, CISA, CEH, OSCP, AWS, AWWA, etc.)
Virtual ISO Programs that bridge the communication gap between IT and OT networks
Organizations in Arizona face increasing cyber threats due to the rapid digitization of their networks and systems. At InfoSight, we provide comprehensive Penetration Testing services to identify vulnerabilities unique to the region's business landscape. Whether you operate in the healthcare, finance, or education sector, our assessments cover critical aspects of your IT infrastructure, including applications and network security. Arizona businesses can greatly reduce their risk of falling victim to cyberattacks by proactively addressing vulnerabilities that could otherwise be exploited by malicious actors.