Home / Services & Solutions / Advisory Services / Security / Penetration Testing
Penetration Testing reduces the risk of successful cyberattacks by attempting to exploit identified vulnerabilities before a bad actor does. At InfoSight, our experts identify security issues beyond the capability of automated tools, taking a more comprehensive approach to testing. With our Penetration Testing Service, you can trust that your security is in the hands of industry authorities.
Our assessments are goal-oriented and designed to test not just your network but also your applications, APIs, mobile apps, web apps, and SCADA/ICS networks. Additionally, we evaluate your organization's ability to respond to security incidents, ensuring a robust security posture. With our Penetration Testing Service from InfoSight, you can be confident in your defenses.
*US-based Expert Ethical Hacking Team.
*Videos to demonstrate successful exploits of your environment!
*Executive Summary Reporting designed for C-Suite and 3rd party.
*Access to Mitigator Vulnerability Threat Manager Platform which includes features such as:
✓A Centralized Dashboard analyzes vulnerabilities, track trends and facilitates scheduling vulnerability remediation tasks.
✓Analyze vulnerabilities by asset, system host, criticality, IP address and search over specific time periods.
✓Create Remediation tickets for your team with the click of a button from within your ITSM or use our built-in ticketing system. Supports API integration with JIRA, ServiceNow, Connectwise, etc.
✓Eliminate duplicate findings on reports where remediation is complete to the highest level and adjust risk scores based upon context and compensating controls to create accurate risk reporting with full change audit tracking.
✓Request "on-demand" Pen Testing of specific vulnerabilities.
✓Request Remediation Assistance (add-on feature).
✓Our Policy & Program Center provides templates for Incident Response, Information Security, BCP, IT Policies, and more.
✓Leverage our Employee Cybersecurity Awareness Training courses.
✓Protect your organization from social engineering attacks with our Email Phishing tool containing hundreds of prebuilt templates.

Our reports are comprehensive, providing both in-depth technical reports, and executive-level reporting is provided to suit your C-Suite, BOD, and 3rd party audit audiences.
Reports feature Videos of actual exploits of your systems, where applicable.
Detailed Remediation Instructions are provided, and you can track remediation activities in Mitigator.
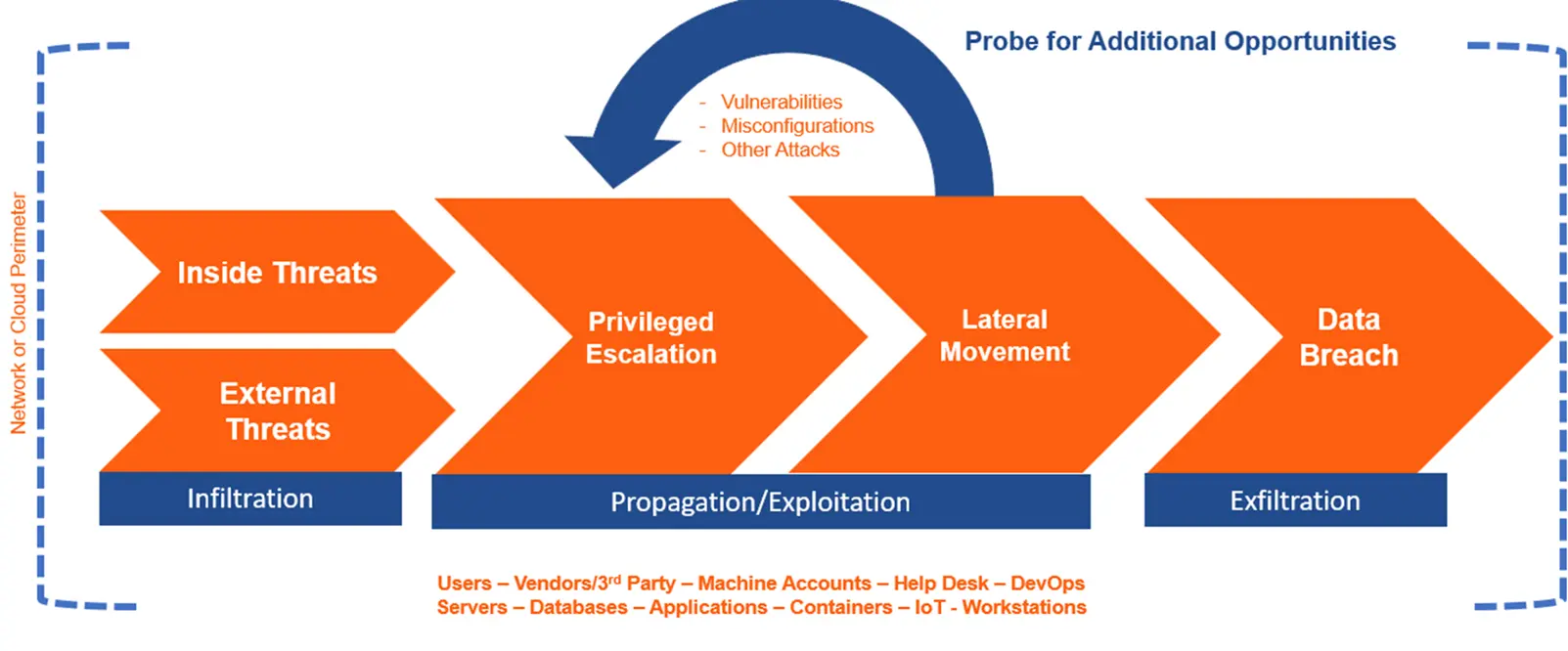
Evaluate environments for real-world readiness
Reduce the risk of a successful attack before it occurs
Identify security issues beyond the capability of automated tools & assessments
Exit interviews to provide both executive level and detailed reports
Reduce the risk of a successful attack before it occurs
Goes beyond typical penetration testing to involve mission-oriented Red Teaming operations
Prioritize your risks and quickly take the right preventative measures
Assists in implementing a Continuous Threat Exposure Management (CTEM) strategy
24x7x365 US-based SOC/NOC
25+ years Regulatory Compliance experience (GLBA, PCI, HIPAA, NERC, AWIA, etc.)
SOC 2 Certified
Offering comprehensive cybersecurity Awareness Training Solutions
Managed Services for On-premise Data center, Cloud and Hybrid environments
Flexible pricing models that can be 24x7, 8x5, OR off-peak 7pm to 7am only coverage
MSP & MSSP Solutions for both IT & OT ICS environments
Certified Experts (CISSP, CISA, CEH, OSCP, AWS, AWWA, etc.)
Virtual ISO Programs that bridge the communication gap between IT and OT networks
